The Google Play Store now has hundreds of thousands of apps that They try to beat each other to reach those top downloads and that thousands of users install them to earn hundreds of euros thanks to that invasive advertising that some integrate to offer some features. Most are of high quality and others go unnoticed so that others have to be careful with them. Luckily they are counted on the fingers of one hand and there are security firms that are in charge of scanning the Android store to find those that may seem "good" but that, when push comes to shove, are quite malicious.
Now there are 13 malicious apps that Google has completely banned from the Play Store thanks to the investigations found by a Lookout. These apps have been removed for violating the ToS, and from what we have been able to find out, some of them have been downloaded millions of times. They have been caught downloading other malicious apps that left positive reviews. Part of them also played asking for ROOT access so that they could install malicious code that survives even a factory reset and what many users have had to face taking a great disappointment without knowing what happens.
What are those 13 apps?
La BrainTest malware family looks like it's back and there are several variants that are responsible for taking ROOT privileges in order to persist in the guts of the phone even when a factory reset and other efforts are made to eliminate them.

It has been Lookout, that already we spoke at the time of this security suite, which has been discovering a series of apps in the Play Store that seemed suspicious, since behind them were developers related to that family of malware known by Brain Test. The funny thing about the case is that these apps had hundreds of thousands of downloads and at least an average score of four points, something that shows the satisfaction of the users and that allows many users to install them, unsuspecting them.
On December 29, the suspicions were confirmed and there were 13 apps found that were related to that group of developers that they are responsible for launching malicious code from apps that seem "normal". Lookout contacted Google and directly banned those 13 apps from the Google Play Store.
How did they get to the Play Store?
This is the question that many of us ask ourselves, how can it be that these normal-looking apps are at ease in the Android store where millions of users can install them without knowing that the wolf comes disguised as a sheep.
From what seems to be these malware authors were using names, games and different techniques to see what kind of apps they could publish in the Play Store without being "caught". Just before christmas an app called Cake Tower received an update. This activated a function similar to the initial versions of Brain Test and included a new server command and control, which was exactly what was needed for the relationship with the other apps.
The explanation for the reviews obtained with good scores is due to the fact that some of these apps are fully functional video games and they hook like so many thousands of titles. Some are even capable of using devices to download and review other malicious apps created by the same authors in the Play Store. All this leads to an increase in the number of downloads.
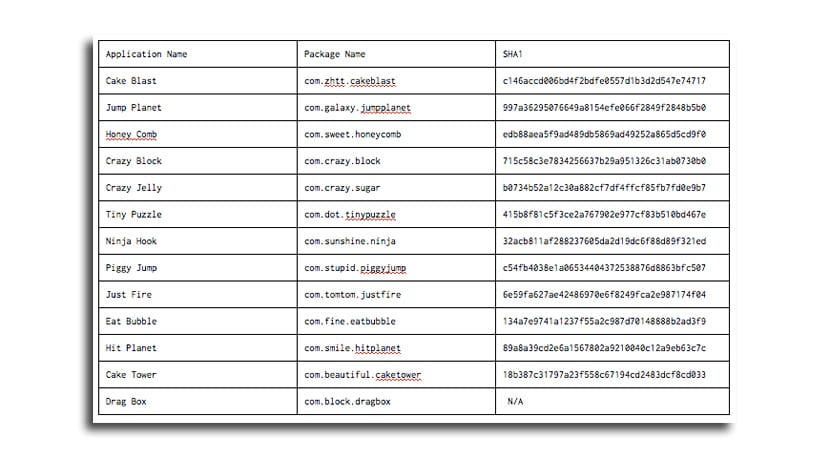
All the thirteen apps removed:
- Cake blast
- Jump planet
- Honey Comb
- Crazy block
- Crazy jelly
- Tiny puzzle
- Ninja hook
- Piggy jump
- Just fire
- Eat bubble
- hit planet
- Cake tower
- Drag box
13 undesirable apps that are safe Outlook will keep finding more for Google to remove them. The problem with this is that in the time that passes from when they are with their malicious codes until they are found, thousands of users download and install them.
