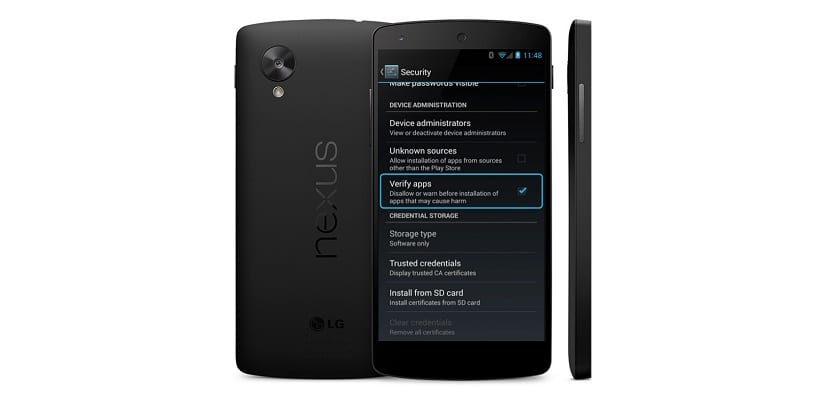
Google announced yesterday a improved security on Android. It will be in charge of continuously monitoring the applications that are running to verify if they are safe. An important advance for Android devices in terms of security.
You have to know that Android received another security improvement sooner than later. check applications before they were installedAlthough this new feature will employ Google's app scanning technology that it uses for the app store.
If, for whatever reason, the operating system detects a problem with an application, this will notify the user with a very similar message at the same check when we are going to install an application that is suspected of being malicious.
With this new functionality what Google wants is having another layer of security as they are usually done with other systems or the same video surveillance of a house by putting cameras to better protect it.
Google has been spreading security services on Android, from apps being verified before installation, warning of potentially malicious applications and now, with constant monitoring on the device. These security "layers" are present in Google Play since Android 2.3, so we could say that most Android devices have them.
Although the percentages are very low in relation to the applications that may have bad intentions, with 0.18% of users who have received an alert message for an app that could be malicious, Google wants its operating system to be as secure as it can be.
What we do not know is that it will affect the system as it is always monitored, especially in terms of battery life, since it is assumed that a process would be added that will always be present in the background.
