
Without going to compare the current society with that described by George Orwell in his book 1984, each time we are more controlled due to our use of the internet. Without the internet, it would be much more difficult to track the activity of citizens, an activity that always leaves a trace through an IP.
The IP with which we surf the internet is like our license plate, a universal license plate that always points to us. No two IPs are the same in the world. Each user has an IP, IP associated with the ISP (internet provider) and who stores a complete record of all our activity through the internet.
To prevent our ISP from knowing at all times which web pages we visit, which we download from the internet and so on, the only solution is to hide the IP. If you want to know how to hide IP on AndroidBelow we show you all the possible options, both free and paid.
Use a VPN
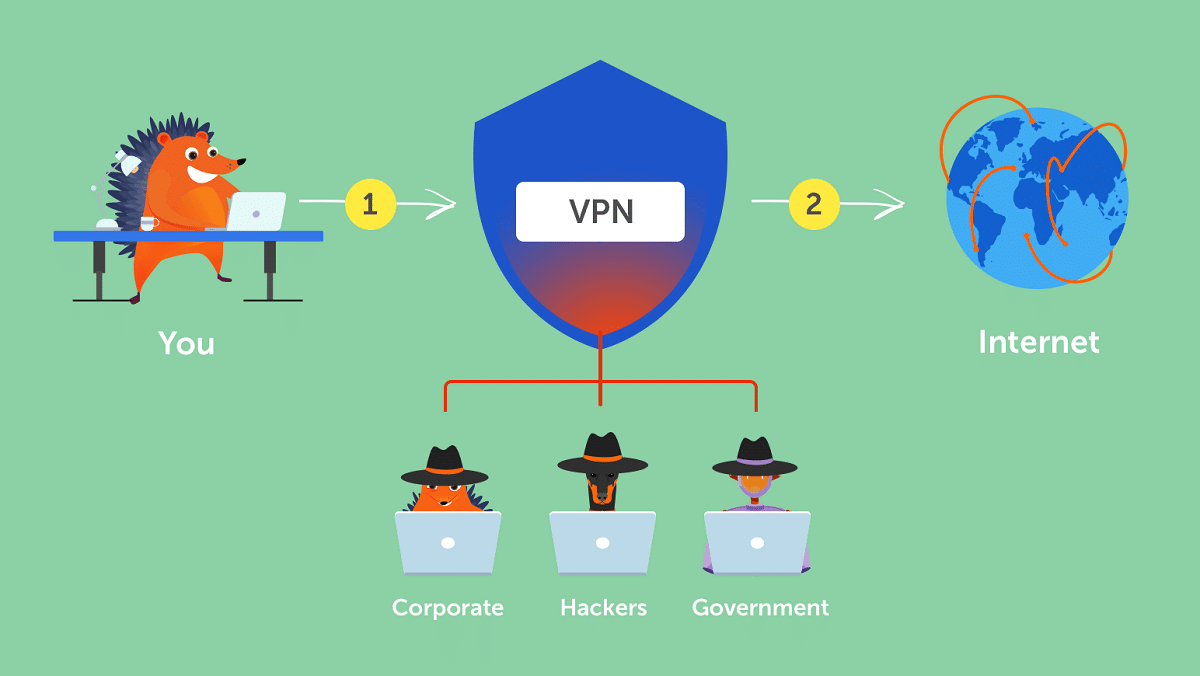
Once we know what the IP is, we must talk about VPN services. These services create virtual private networks (VPN for its acronym in English) between our equipment and its servers, so that our ISP does not know what we are using their internet connection for, and it cannot track all of our activity.
In addition, all the content that we send and receive to our VPN, is fully encrypted, so no one will be able to access your content if you manage to get hold of it, although if you have a lot of free time (years) you will be able to decrypt it at some point.
Also, when using a VPN service, we will not navigate with our usual IPInstead, we are going to use an IP from the country that we have previously selected. This is one of the main characteristics of these services, since in addition to hiding our tracks, they allow us to access geographically restricted content.
Not all VPNs are the same
Paid VPNs do not store any record of our browsingTherefore, no government or police body can request a browsing record to verify what we do with our internet connection.
However, not only can we find paid VPNs, but there are also free ones. These platforms have to make a living. The source of income is obtained trading with our browsing data with advertising companies, analytics ...
When choosing a VPN if we want to browse completely anonymously and that our data is not stored in any type of registry we must choose a payment platform. Some of the best known VPNs are NordVPN, TunnelBear, ExpressVPN, Surfshark ...
The only drawback we face when using a VPN is that they do not offer us the same access speed that we can have browsing directly with our connection without any type of protection, so we must take this into account when choosing the VPN that offers us the highest speed.
Use a proxy
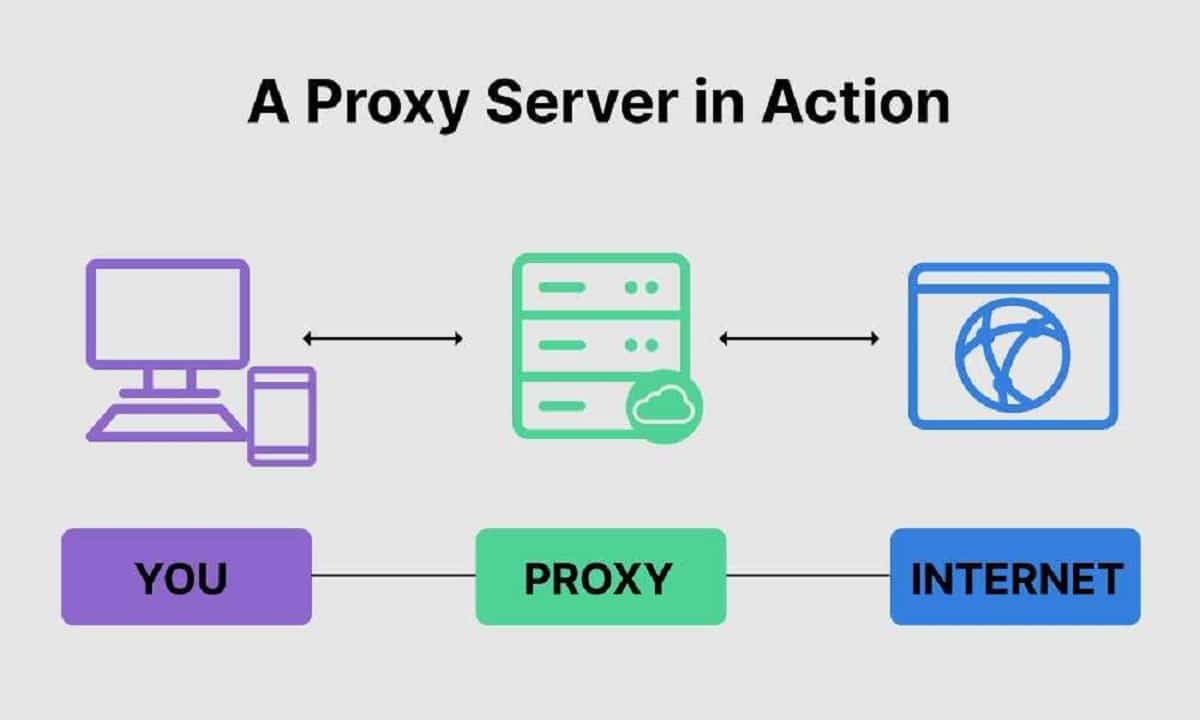
A proxy is a computer that acts as an intermediary between a client's connections (U.S) and a server. In this way we use the IP of the proxy, not that of our team.
If it is a company proxy through which all computers connect to the internet, It is very difficult to know which equipment the IP corresponds to unless the administrator uses a program that records the communications of all computers.
Tor Browser

Tor Browser is a browser mainly used for access the Dark Web, not to be confused with the Deep Web. This browser connects to the Tor Project servers and allows browse anonymously using an IP different from ours.
It works similar to VPNs, but unlike these, we cannot choose the country from where we want to connect. In addition, the browsing speed it is much slower than the connection speed that we can have contracted, slower than we can find it in VPNs.
The best of all is that it's completely free and it does not require any payment to be able to use it whenever we want. In addition, it incorporates a system that prevents the web from tracking us and an ad blocker.
Best of all, Tor Browser is not only available for Android, but also, also available for desktop operating systems like Windows, macOS, and Linux.
Use a public Wi-Fi

The simplest solution if you don't want to complicate your life hiding your IP is using a public Wi-Fi connection. Routers that offer these types of public connections do not keep a record of all connecting devices.
However, some may be configured to store the mac (the license plate of our device not the connection) as well as the type of device for statistical purposes only, since through this data they cannot track the owners.
The mac is the internet identification system of all the devices that connect to the internet and it is unique per device.
You should not use this type of public connection to access our bank accounts from a browserSince a friend of someone else may have connected to the same network who is tracking all activity to collect information on logins.
You can connect to any service without problem as long as use the application available for it, since the information is encrypted from the device to the servers that give us access.
Do not confuse hiding IP with incognito browsing
All browsers, at least the most widely used, allow the user to browse incognito or anonymously as some describe. Nevertheless, they do not mean that we can navigate by hiding our IP, but we will not leave any navigation traces in the browser.
When using the private, incognito or anonymous browsing mode (as designated by the developer), no data will be stored in the browser, that is, browsing history and cookies will not be stored and other tracking elements will be removed immediately when we close the tab.
This option is valid for when we need connect to the internet from a device that is not ours to consult, for example, our bank accounts, access our social network, visit adult content pages ...
