
Si you are concerned about Android security, you should know everything that you have not been told, since this operating system keeps some secrets that few know. Everything that they have not told you or do not tell you, beyond Google's GMS services, binary blobs, root, and supposed security apps, some of them without much real use against cyber attacks.
Furthermore, it is also important to determine if Android is more or less secure than iOS, and if it really Can we do something as users to improve the security of our mobile devices.
Root or not root: that is the question
Android is based on the Linux kernel, but it is not a GNU/Linux distribution. This Google system is very limited in terms of the capacity that the user has, with many restrictions. These restrictions can be overcome by being root, that is, a privileged user who can do anything. But nevertheless, rooting the mobile has its security risks. Therefore, a rooted mobile is not always safer as some think:
- Advantages:
- Unlimited administration capacity, that is, greater control over the system.
- Superior performance.
- Ability to uninstall bloatware.
- Greater functionality.
- Access to a Linux terminal.
- Ability to make security changes.
- Disadvantages:
- Void the warranty.
- You may be at risk of the device stopping working (or not working as it should) if not done correctly.
- If you download the ROM from the wrong site, it may include dangerous malware.
- Problems with OTA updates.
- Malicious applications have execution privileges, so not only the user could do what they wanted, but also the apps. That is, rooting maximizes the potential damage of malicious code.
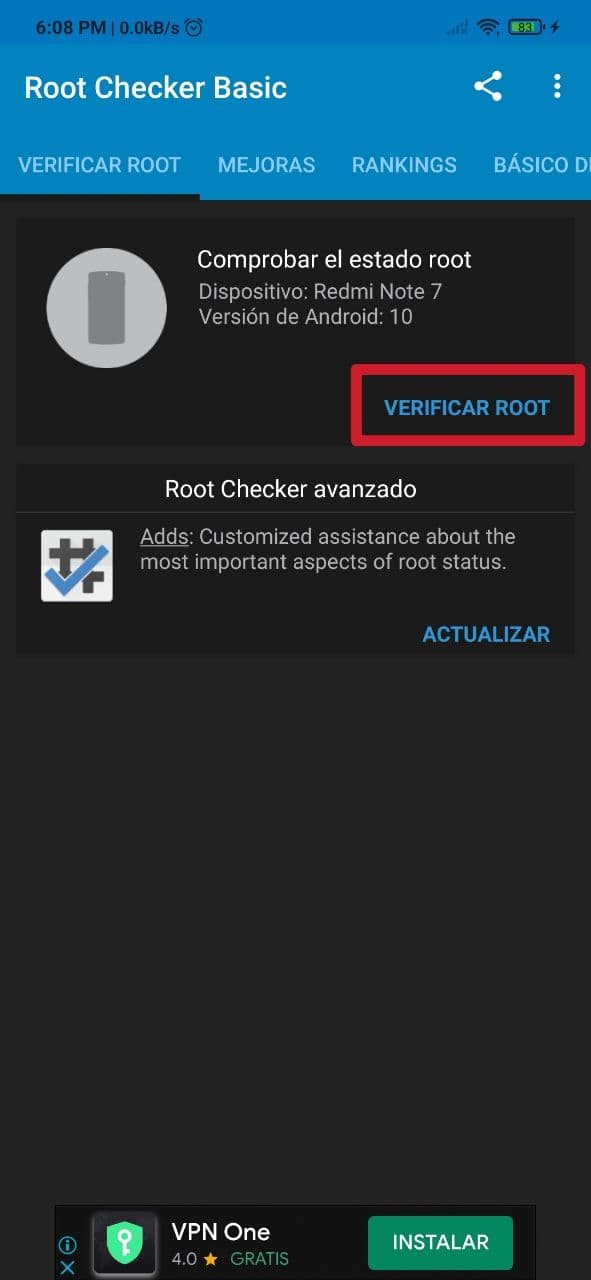
Sometimes your mobile may be rooted without you knowing it, since someone has had access to it and has done it behind your back. The reason for doing this may be to install some kind of spyware. For example, to be able to remotely control your mobile, access the microphone and listen to what you say, or your camera and see what you do, etc. It is much more frequent than you imagine, especially in jealous couples who do not trust each other. To find out if it is rooted, you can use apps like Root Checker, it is very simple, and it will tell you if the root access is installed successfully or not. If it is installed successfully, it will pose a danger to your security.
Android innate security: SELinux

Linux systems generally use AppArmor or SELinux as security modules. In the case of Android, SELinux is used. A module initially developed by Red Hat and the NSA, something that generates distrust in many security paranoids. Also, those who prefer AppArmor not only choose it for that, but it's also a lot easier to manage, whereas SELinux can be too complex to understand and make good use of.
The problem is that Android already comes with a default configuration, and you you can't change it unless you are root. If you see some apps that promise to make changes to SELinux, they are either a scam or need root access to do so. The only thing that can be done is to review the privacy and security settings that you have in Android Settings to see carefully what is allowed and what is not, and leave the mobile as armored as possible.
Google Play: a double-edged sword

La Google Play app store is a double-edged sword. On the one hand, it is very practical to install the apps you need from a reliable source, avoiding downloading dangerous .apk from third parties or unknown sources. These APKs may not be malicious, but in many cases they will be modified with malicious code to steal passwords, access bank details, use your mobile's resources to mine cryptocurrencies, etc.
But the hidden face is that there are millions of apps available, and despite Google's filters, you can always escape some malicious apps that will be available for download (some with similar names or the same as others that are not malicious) and you will be installing malware without realizing it, with consequences that can be very serious, such as using unknown apps and origins. For this reason, it is best to check if the developer of the app you are going to install is trustworthy by searching for information about him on the Internet.
To improve security on your Google Play, you must follow these tips:
- Protect the payment system that you use so that other people (or minors) who have your mobile cannot buy apps or services without your consent. To do this, go to Google Play settings> Payments and subscriptions> Payment methods> there you can manage the active payment methods. On the other hand, to protect payments go to Google Play settings > Settings > Authentication > Require password for purchases > For all purchases made through this device.
- Use the option Play Protect to analyze harmful apps.
Antimalware that doesn't work

Another Android security problem is the anti-virus or anti-malware software that exists on Google Play. Not all of the ones you see work, or don't work as they should. Therefore, do not trust these packages that scan the system for malware, as they could miss very dangerous threats. To be safe, I would recommend you to use these apps:
- CONAN Mobile: is a free app developed by INCIBE and is responsible for analyzing your Android's security settings, analyzing apps, permissions, proactive network monitoring, analyzing whether your email addresses are vulnerable, and offers OSI advice. It is not an antimalware as such, nor is it an antivirus software, but it is a perfect companion for them.
- AVIRA Antivirus: It is a free and easy-to-use antivirus application, although it has a paid Premium version, with extra functions. The reason for this recommendation is that it is an app developed in Europe, for greater confidence, and it does its job quite well.
- BitDefender Mobile Security: another European, and one of the best you can find when it comes to a paid antivirus app. It has a protection system against malware, online threats, information protection, etc.
Use VPN
No matter how good your Android security settings are, and no matter how good protection software you have installed, to make sure that you are not vulnerable to MitM-type attacks, espionage of your passwords, etc., it is best to use a VPN, with much more reason if you telecommute with your mobile device and handle sensitive company or customer data.
Thanks to these services, which are not expensive at all, you will be able to encrypt all incoming and outgoing network traffic, to greater security and that no one can access it, in addition to providing greater anonymity, with an IP different from the real one and without your IPS being able to collect data on network use on its servers.
There are many native VPN apps for Android, but the best three that you should consider and that will allow you to use streaming platforms without problems, are:
- ExpressVPN: perhaps the safest, fastest, most complete and suitable for professional use, although it is also more expensive than other services.
- CyberGhost: the best if you are looking for something cheap, easy, functional, safe, and simple.
- PrivateVPN: a good alternative if you are not satisfied with the previous ones.
Manage app permissions
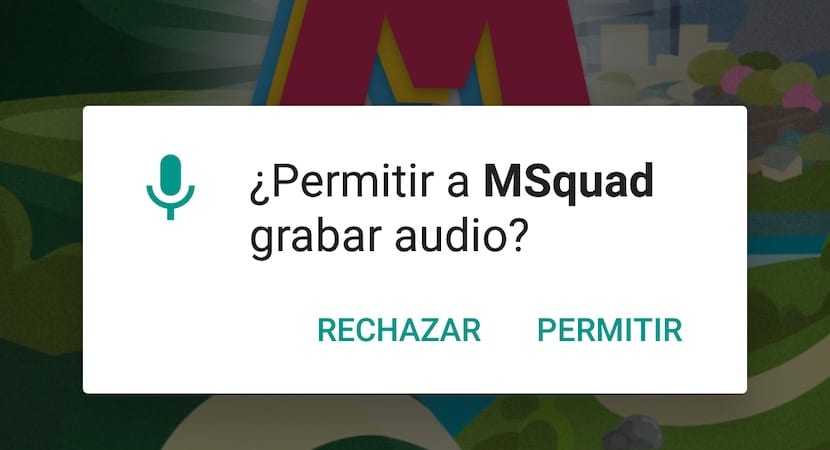
Another essential point to maintain good security and privacy is to manage the permissions of your installed applications well. Not only is it enough to say above, to install those apps that need fewer permissions, but also manage these permissions. User knowledge and common sense also come into play here. For example, going back to the previous case, that flashlight app B that needs permission for the camera, your contact list, and the storage, will be indicating that it is doing something more than lighting. Access to the camera is justified, since you need it to turn the flash light on or off. Instead, access to your address book or storage is likely due to reporting data (using trackers).
There are some apps on Google Play to manage permissions, although they are not necessary, with their own Android settings are enough:
- Go to the Android Settings app.
- Look for the Applications section.
- Permissions
- And there you can see and modify the permissions that each app has.
Updated system
Of course, it is something that I will not tire of saying, keep the operating system (and firmware) updated, as well as the installed apps, is also a nice security enhancement. Keep in mind that the Android system or any of its elements may have vulnerabilities. Being the latest in updates, you will be able to have the latest security patches available, so that this vulnerability is solved and cannot be exploited by cybercriminals.
Do not neglect this part, it is more important than many think. Always remember review pending updates. To update your Android system by OTA (if supported):
- Go to the Settings app.
- Find the system updater (may vary in name depending on the customization UI layer).
- Check for available updates.
- Download and install the updates.
En the case of apps:
- Go to the Google Play.
- Then click on your account to access the configuration menu.
- Go to Manage apps and devices.
- Then go to the Manage tab.
- And update the apps in the list that have pending updates.
In case your Android operating system is of an older version for which there is no longer support and no updates are released, the options are to install a more current ROM on your own, which is not recommended at all, because it may not function properly if it does not have support for your hardware, or consider switching to another new mobile with a more recent version that does have updates by OTA (Over The Air).
Minimize and you will win
Keeping the mobile with the greatest minimalism is another clear advantage for Android security. That is, it it is better that you leave only exclusively the apps that you use frequently, and uninstall all those that you no longer use, as well as the bloatware that the mobile usually comes with from the factory. This will prevent any of the vulnerabilities that any of these apps may have from being exploited to compromise your device. Remember the formula:
less code (less apps) = less possible vulnerabilities
Common sense and distrust: the best weapon

Phishing has become another big problem. To combat this security threat, the best tool you have at your disposal is called common sense and mistrust. They can save you from quite important dangers. For example, some tips are:
- Do not open (let alone download attachments) from suspicious emails. The most suspicious usually come from fraudulent emails posing as banking entities, Post Office, Endesa, Telefónica, Tax Agency, etc., thus claiming alleged debts that you have. They are also frequent those who give you something without conditions. Sometimes they can be messages in Spanish, other times they could be in another language like English, something even more suspicious.
- don't pay attention spam calls or that they ask you for bank details, access to services, etc. A bank or company will never ask you for these credentials over the phone. If they do, it's a scam.
- The same can be applied to SMS and other messages that they can arrive through instant messaging apps such as WhatsApp, and that ask you for passwords, codes, etc., or that they are people that you do not have added in the agenda. Always be suspicious of it and don't send anything. Many times they seek to impersonate your identity for crimes.
- do not enter suspicious websites and much less access pages of your bank or other services where you are registered from links that come to you by email, etc. They can be baits for you to enter your access data and they will keep them, redirecting you to the real web. Cybercriminals have perfected these methods so much that sometimes it is impossible to distinguish the fraudulent website from the real one with the naked eye, even with an SSL (HTTPS) certificate.
- Periodically review your accounts, if you suspect suspicious access, use two-step verification where possible, or change your password.
- When in doubt, be cautious and don't risk it.
backup policy
Although in Android systems a lot of data is sync with the cloudsuch as contacts, calendar, messages from instant messaging apps, etc., it is important that you have a proactive backup policy. It does not hurt that from time to time you make a backup of all your data on a pen drive or an external storage medium.
This will avoid problems, such as those that could bring you a breakdown in your mobile device that makes you lose all the data, or threats such as the ransomware, by which they encrypt your data and ask you for a payment in exchange for giving you the password so that you can access your data again.
Strong passwords
The passwords you use must meet a series of minimum requirements to be safe:
- They should have at least 8 or more characters long. The shorter, the more vulnerable to brute force attacks.
- Never use passwords that can be easily guessed by social engineering, such as the name of your pet, a specific date such as your birthday, your favorite team, etc.
- Never use words that are in the dictionary as a password, or you will be vulnerable to dictionary attacks.
- Don't use a master password for all. Each service (email, OS login, bank,…) must have a unique password. Thus, if they find out one of them, they will not be able to access other services. On the other hand, if a teacher discovers you, they can have access to all the services, with the damage that this implies.
- The strong password must be a mixture of letters lowercase, uppercase, symbols, and numbers.
For example, a strong password template would:
d6C*WQa_7ex
To be able to remember these long and complicated passwords well, I recommend you use a password manager like KeePass. That way you won't have to remember them, and you'll have them in an encrypted and secure database.
Privacy: a right

La privacy is a right, but it is a right violated day by day by large technology corporations that use personal data that they analyze with Big Data to obtain some kind of benefit, or that they sell to third parties for very juicy amounts of money. In addition, cybercriminals are added to them, who could use this stolen personal data for theft, for blackmail, for sale on the deep/dark web, etc.
Try give as little data as possible, and minimize their leakage. In cybersecurity attacks, one of the first stages is called “information gathering”, and the more information an attacker has about you, the easier the attack will be and the more impact it will achieve.
Some tips for it are:
- Use safe instant messaging apps.
- Also use secure web browsers that are more respectful of your privacy. Some recommendations are Brave Browser, DuckDuck Go Privacy Browser, and Firefox. Also, don't forget to access their settings and block pop-ups, cookies, history, stored log data, etc. If you can, browse in incognito mode.
Protection against theft

Many antivirus software have anti-theft function, with which to be able to detect by GPS where your mobile device is, and even send a command so that all data is remotely deleted and thus the thief (or whoever finds your mobile in case of losing it) cannot have access to sensitive data, such as banking, etc. It is important to activate this type of functions in case one of these thefts occurs. Do not rely on PIN, or screen patterns, access passwords, etc., they are additional positive barriers, but it is best not to challenge the ingenuity of the suspect.
For this, I recommend you install the Google app for Android Find my device, or what you use the web service. If you have the location activated on your mobile, you will be able to locate it, make it ring in case you have lost it so you can find it, and erase the data remotely for security.
Safe networks, dark networks

For strengthen your networks On mobile devices, you should keep in mind three fundamental points that improve Android security:
- don't connect to untrusted wireless networks, from BT at your fingertips, or free WiFi networks. They can be decoys to gain easier access to your device.
- Don't you use them? Turns off. Not only do you save battery, you can also disable WiFi network, Bluetooth, NFC, Data. Airplane mode can also be a quick fix to activate, though keep in mind that you won't have a line either.
- Analyze if you router has some vulnerability. If so, update your firmware if there are security patches. For example, with the WiFi Analyzer app. There are also other interesting apps like Fing, WiFi WPS/WPA Tester, etc.
Unknown sources and ROMs
Of course, you should always have the permission to install apps from unknown origins off on your Android system:
- Go to Settings.
- Finding “Unknown Sources” in other UI layers may be called something different, such as “Install Unknown Apps” or similar.
- Go inside and you can disable it or see the current system apps that have that permission (there shouldn't be any).
As for the the roms, if you don't decide to install a different version on your own, or root, you should have no problem in this regard. Only those who decide to install a different ROM can run into these problems, by downloading ROMs from third party (unofficial) websites, which have been altered with malicious code. Therefore, always download from official websites.
Binary Blobs, Proprietary Software, and Other Risks
Other security problems against which all users are totally unprotected, regardless of the configurations and security plugins you use, are those that out of the user's control:
- Software:
- Proprietary or closed code: when proprietary or closed source apps or services are used, there is no access to the program's source code and it is not known for sure what it actually does (backdoors to allow remote access without the user's consent, tracking of data, the famous bidirectional telemetry that some call it, intentional or unintentional vulnerabilities, bugs, etc.), apart from the functions for which it was apparently designed. Even if a security problem is detected, the software developer is the only one who can correct it and supply the appropriate patches. But for that, you have to trust the good work of the developer and the will to do it quickly.
- Manipulation in the open source supply chain: free and open source software does not escape many of these evils either. Source codes could be modified to intentionally introduce vulnerabilities, or back doors, as well as other types of malicious code, etc. It is not the first time that it happens, so you should not trust 100% either. However, the positive thing is that anyone can look at the source code and find such problems and even patch them on their own. Therefore, it is much more difficult to hide something in files that are exposed to the whole world (open) than in ones that only a company or developer has access to (closed).
- Kernel:
- binary blobs: These are the modules or controllers (drivers), as well as the firmware, which is closed source or proprietary and is in the Linux kernel, put there by companies that include certain functions to support their devices. Many are suspicious of these opaque parts, since they would have the same dangers as closed software with an aggravating circumstance, they do not run in user space, but in privileged space, which is why they can be much more harmful.
- Bugs and vulnerabilities: of course, neither Linux nor any other operating system kernel is 100% secure, it also has vulnerabilities and bugs that are detected and corrected with new versions and updates, although it is also true that as new versions come out, there are possibilities that other possible vulnerabilities or bugs are added that were not present before. Something that happens with all systems and software in the world, whatever type it is.
- Hardware:
- Torjan Hardware: Lately there is more and more talk about modified hardware to include hidden functions in it, or to make it more vulnerable. These types of modifications can be made from the RTL designs of the chips, through the last stages of development, even once the final design has reached the foundry or semiconductor factory, altering the masks for photolithography. And these problems are extremely difficult to detect, if not impossible. So if any government or entity wanted to introduce a security threat to their enemies, this would be the best method.
- Vulnerabilities: Of course, even if unintentional, there can also be hardware vulnerabilities, as seen with Spectre, Meltdown, Rowhammer, etc., and these types of side-channel attacks can expose highly compromised data, such as passwords .
Removable battery, tabs for cameras and security switches

You should know that even when the mobile turns off and the battery is exhausted, there is some power left and the terminal could be tracked. Therefore, many criminals, to avoid tracking, use old mobiles or those that can be removed from the battery to take them completely offline. Unfortunately, even if it is not to commit a crime, but to be 100% sure that the mobile is not reporting anything, it is rare that you can remove the battery, almost all of them have it integrated.
Some terminals, such as the PinePhone from Pine64, and other brands dedicated to creating secure mobile phones and to improve privacy, have added hardware switches for the shutdown of sensitive modules. That is, some physical switches with which you can turn off parts such as the camera, the microphone, or the WiFi/BT modem, to be safe when you are not using these elements.
Since the vast majority of models do not have it, one of the few things we can do to prevent eavesdropping by camera of the device, it is simply buy tabs to cover this when you don't use it. However, the current multi-sensor systems for the rear or main camera of mobile phones have made this a little more difficult, although it is still possible on the front. Some mobiles include details to improve privacy such as a camera that can be hidden, which is also appreciated.
I would not like to leave in the inkwell biometric sensors, such as fingerprint readers, facial or eye recognition. This data is also sensitive, and unique, so it's not a good idea for it to fall into the wrong hands. Unfortunately, manufacturers are making it harder and harder to get around them. For example:
- They have gone from putting the fingerprint sensor behind the mobile or at one end to putting them under the screen itself, or in the on and off button, so you have no choice but to use it.
- There are also developments and patents for cameras under the screen itself, another obstacle to cover it up.
Memory card and USB cable: be careful where you put them

Beyond everything said above, another aspect to which to pay attention to is the memory card and USB data port. They are elements for which we must not forget that they can be used as entry vectors for malware. To avoid it:
- Do not connect the Android phone via USB cable to an unknown computer, such as Internet cafe, public library, etc.
- Don't insert the microSD card into computers you don't trust either, it could get infected and then infect your mobile device when you put it.
- And, much less, use a microSD that you find, it could not be an oversight, but an intentional act for you to use it and infect yourself with some malware.
Turn off debugging now!

El debug mode, or debugging, of Android, can be useful to access certain functions or information important for developers, or in certain specific cases. However, you shouldn't have it active as a rule, as some attacks could take advantage of it. To disable this mode:
- Go into Android Settings.
- You can search the search engine for “developer” and Developer Options will appear.
- Go in, and disable this option.
Does the origin of the smartphone matter?

LG Wing with swivel display
Last but not least, you should always choose brands that are not on blacklists from certain governments for their dubious security (and I am not referring to brands "punished" by geopolitical wars). Much better if they are European, although in that sense there is not much to choose from. For example, the FairPhone, which is from the Netherlands and aimed at improving security, user privacy, and more sustainability.
Another option is to use devices mobile phones specially oriented to security, privacy and anonymity. Magnificent options for professional use, such as those of Silent Circle, although if you take into account all the tips in this tutorial, you can choose the one you prefer, and obtain good levels of security.


