Every operating system is vulnerable to threats, so is the Android system of Google. Although the vulnerabilities are not too many in recent times, it is always good to know what they are and how they affect our phones that are not usually updated regularly in many cases.
Google has warned of a new vulnerability known as CVE-2020-0096 and is called StrandHogg 2.0 by the Norwegian company Promon, which would be the second version of the well-known threat that appeared in December last year. It has many similarities and they are hard at work releasing a patch.
StrandHogg Background (2019)
StrandHogg was recognized as a weakening of the system in early December, affecting Android multitasking and allowing legitimate applications to be spoofed by malware. In many cases the intervention was unnoticed, it affected version 6 to 10, there was malware at that time that used the vulnerability to activate itself without the need for root permissions.
At that time, up to 36 applications were compromised, they had malicious code that endangered Android and almost 500 applications, quite a few used by users. If a hacker took control through StrandHogg, he could perform various actions, including being able to hear the person through the microphone, read and send SMS, access contacts, record conversations, access the Gallery, among many other things.
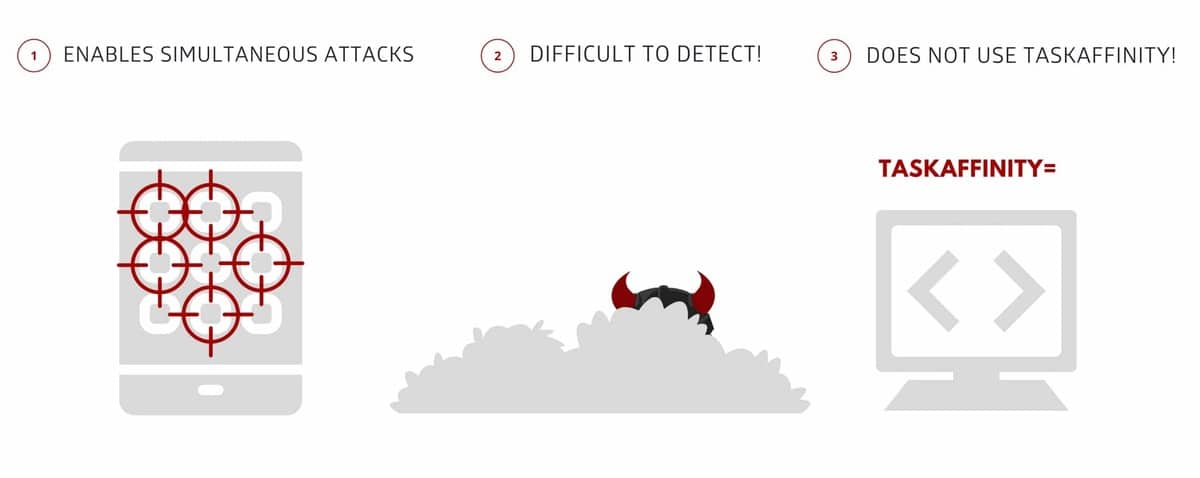
This is the new and dangerous malware StrandHogg 2.0 CVE-2020-0096
StrandHogg 2.0 assumes a similar result, although it uses a different method. Instead of using Android's multitasking functions, the new vulnerability uses a function called mirroring, a technique that will allow malicious apps to decide to masquerade as others in a hidden way.
Hackers can use a malicious tool installed on your device to gain permission to access private data, they can even attack several Android terminals at the same time, the previous one was nothing more than one attack per session. In this case, access becomes identical in this case, they can access SMS, images, GPS location, spy on cameras and various other actions.
Protect yourself from StrandHogg 2.0
In this case, it is necessary to have common sense not to be hunted by this vulnerability, all before Google releases May patch for Android. Among the tips is not to download apps from pages outside the Google Play Store or access porn pages which could compromise your smartphone and data.

The recommendation in this type of case is to avoid downloading suspicious applications, so before downloading one, check if the application belongs to a well-known company and always be wary of tools that promise to make your phone more secure.
Is my Android device in danger
StrandHogg 2.0 CVE-2020-0096 does not affect the latest version of Android, but yes to the previous versions of Android, which according to Google are installed in 91,8% of the phones. It is advisable to keep the device updated with the latest manufacturer updates.
Google promises to launch the update before the end of May and still has several days to tackle this problem that would affect many of the devices because they do not have the recent version of Android.
Source: Europa Press